HTTP Methods

What is HTTP ?
HTTP stands for Hypertext Transfer Protocol. It is a protocol used for transferring data over the web, specifically between a client (usually a web browser) and a server. HTTP is the foundation of data communication on the World Wide Web.
What are the HTTP Methods ?
- GET
- POST
- PUT
- HEAD
- DELETE
- PATCH
- OPTIONS
1. GET
- Purpose: The
GETmethod is used to request data from a specified resource on the server. It is the most common HTTP method, primarily used for fetching resources like web pages, images, or data from APIs. - Key Characteristics:
GETrequests are safe (they don’t modify data) and idempotent (repeated requests will always return the same result). It is used to retrieve information without making any changes to the server.
2. POST
- Purpose: The
POSTmethod sends data to the server to create or update a resource. It is commonly used when submitting forms or uploading files. - Key Characteristics:
POSTrequests are not safe (they may change data on the server), and they are not idempotent (repeating the request could create or modify resources multiple times). It’s typically used for sending data that will be processed or stored.
3. PUT
- Purpose: The
PUTmethod is used to update or replace an existing resource on the server. If the resource doesn’t exist, it can create a new one. - Key Characteristics:
PUTis idempotent, meaning that making the same request multiple times will result in the same state. It replaces the entire resource, unlikePATCH, which only updates parts of it.
4. DELETE
- Purpose: The
DELETEmethod is used to remove a specified resource from the server. - Key Characteristics:
DELETErequests are idempotent, meaning if you delete a resource and then delete it again, the result is the same (the resource remains absent). It’s used when you need to remove data from the server, like deleting a file or database record.
5. HEAD
- Purpose: The
HEADmethod is similar toGETbut retrieves only the headers of a resource, without the body. It’s often used to check metadata or verify if a resource exists without downloading it. - Key Characteristics: Like
GET,HEADrequests are safe and idempotent. It’s useful for checking the status of a resource, like checking for file existence or size without downloading the content.
6. OPTIONS
- Purpose: The
OPTIONSmethod is used to query a server about which HTTP methods it supports for a specific resource. It is commonly used in CORS (Cross-Origin Resource Sharing) scenarios to determine the allowed operations before making a request. - Key Characteristics:
OPTIONSrequests are safe and idempotent, and they provide information about the server’s capabilities without modifying any resources.
7. PATCH
- Purpose: The
PATCHmethod is used to apply partial updates to a resource, unlikePUT, which replaces the entire resource. It’s used when only specific fields or attributes need to be modified. - Key Characteristics:
PATCHrequests are not idempotent (by default), as sending the same patch multiple times may yield different results. It is used for partial modifications of a resource without needing to send the entire data.
8. TRACE
- Purpose: The
TRACEmethod is used for diagnostic purposes. It allows the client to see the path that the request takes to reach the server, including all intermediate proxy servers. The server responds by sending back the exact request it received, which helps with debugging and tracing how the request is being handled by proxies or intermediaries. - Key Characteristics: The
TRACEmethod is safe (it doesn’t modify any data), but it is not idempotent (it may vary based on the proxies or intermediaries along the request path). It’s primarily used for diagnostic or troubleshooting purposes to track the request’s journey through the network.
- Note: In practice, the
TRACEmethod is rarely used in production environments due to security concerns, as it can potentially expose sensitive information and headers. Many web servers disable it to mitigate certain types of attacks like cross-site tracing (XST).
Latest Posts
- All Posts
- Software Testing
- Uncategorized

March 3, 2025

February 28, 2025

February 28, 2025
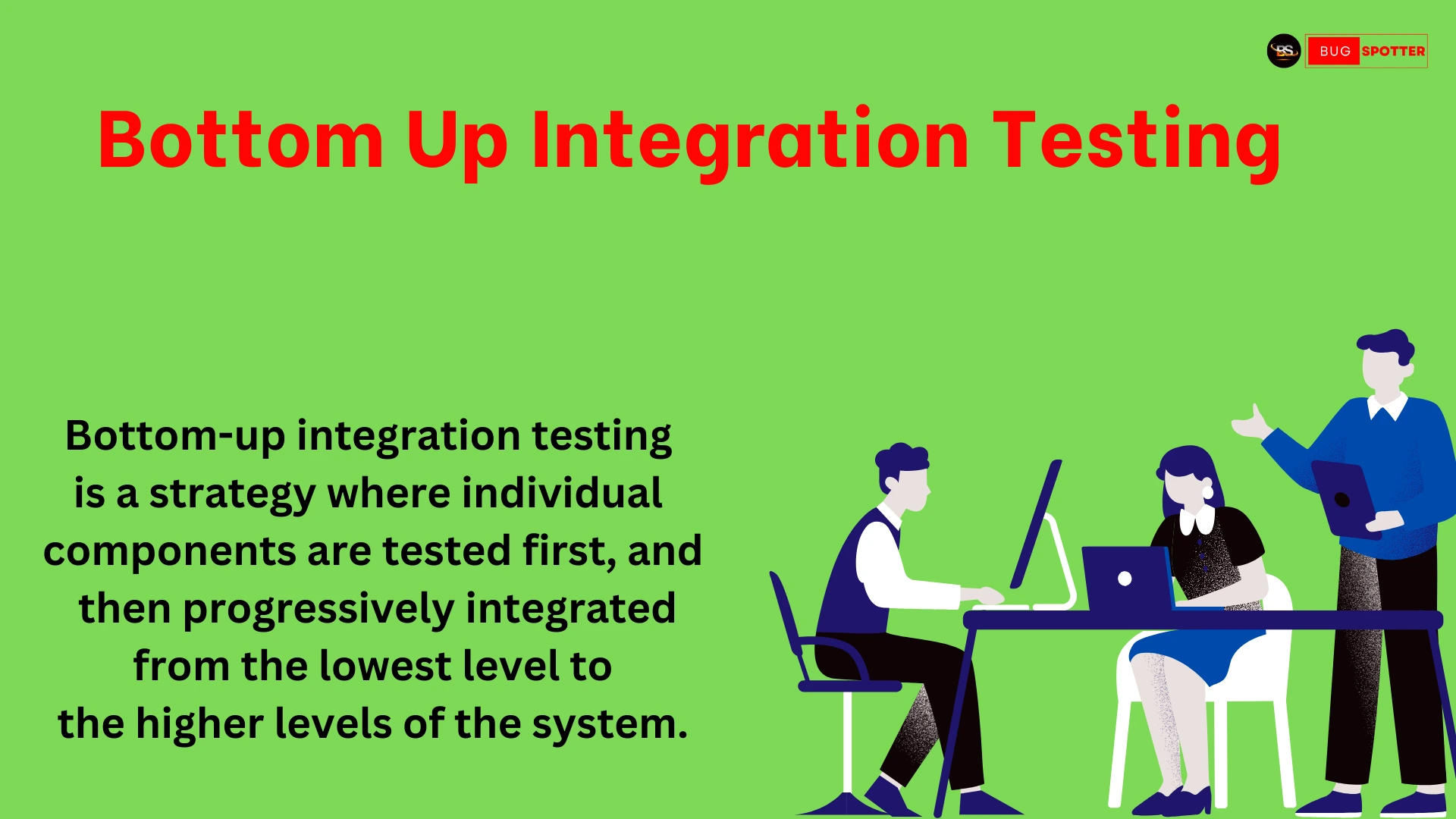
February 26, 2025

February 25, 2025
Categories
- Artificial Intelligence (5)
- Best IT Training Institute Pune (9)
- Cloud (2)
- Data Analyst (55)
- Data Analyst Pro (15)
- data engineer (18)
- Data Science (104)
- Data Science Pro (20)
- Data Science Questions (6)
- Digital Marketing (4)
- Full Stack Development (7)
- Hiring News (41)
- HR (3)
- Jobs (3)
- News (1)
- Placements (2)
- SAM (4)
- Software Testing (70)
- Software Testing Pro (8)
- Uncategorized (33)
- Update (33)
Tags
- Artificial Intelligence (5)
- Best IT Training Institute Pune (9)
- Cloud (2)
- Data Analyst (55)
- Data Analyst Pro (15)
- data engineer (18)
- Data Science (104)
- Data Science Pro (20)
- Data Science Questions (6)
- Digital Marketing (4)
- Full Stack Development (7)
- Hiring News (41)
- HR (3)
- Jobs (3)
- News (1)
- Placements (2)
- SAM (4)
- Software Testing (70)
- Software Testing Pro (8)
- Uncategorized (33)
- Update (33)