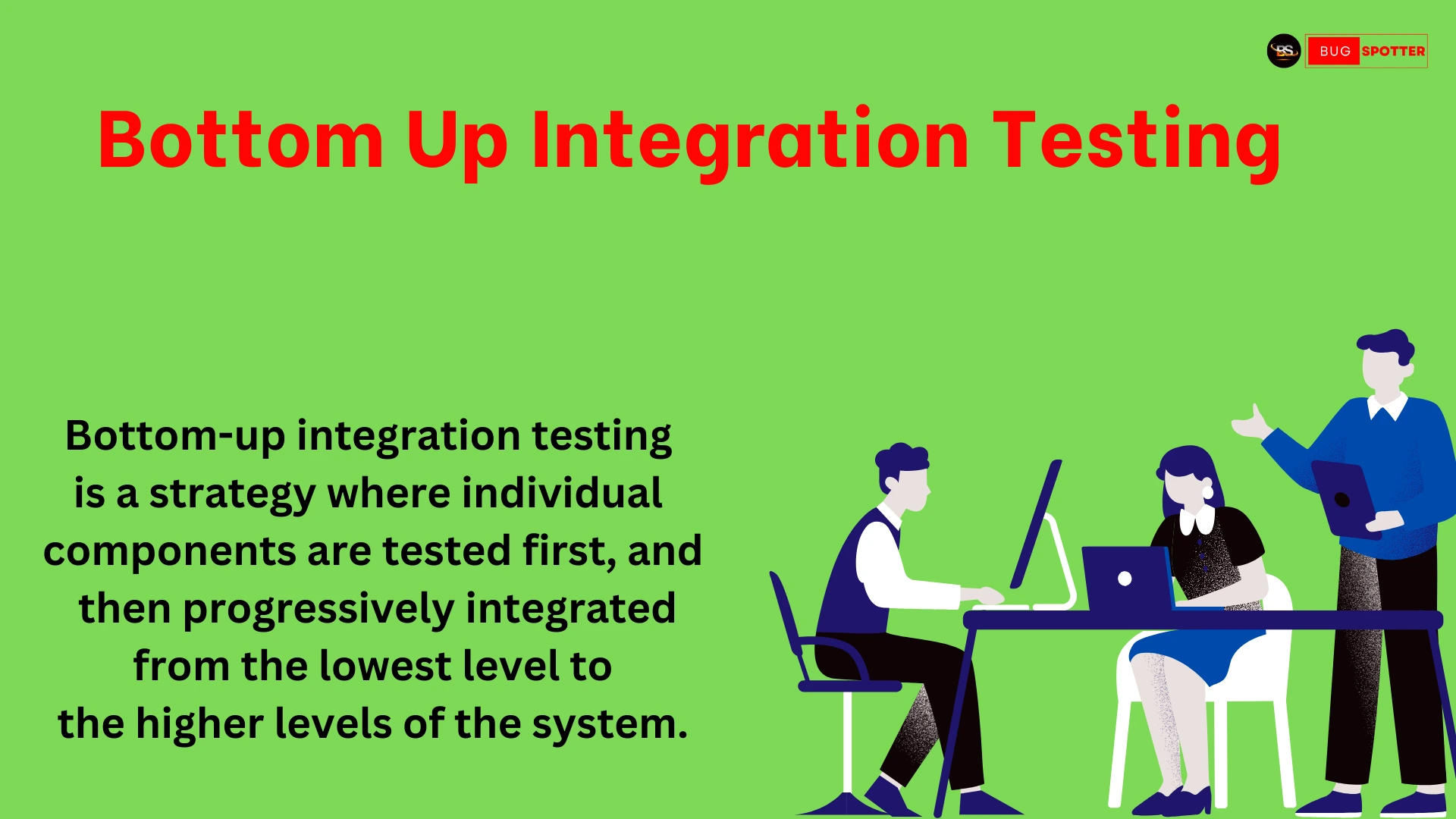
What is Quantum Cryptography?

Quantum cryptography is a field of cryptography that leverages the principles of quantum mechanics to secure communication and protect data. It aims to exploit the fundamental properties of quantum physics, such as superposition and entanglement, to create secure methods of encryption that are theoretically immune to the capabilities of classical computing, even with the advent of quantum computers.
Introduction to Quantum Cryptography
Quantum cryptography uses quantum mechanics principles to provide methods for secure communication. Unlike traditional cryptographic techniques, which rely on the difficulty of mathematical problems (like factoring large numbers), quantum cryptography depends on the fundamental rules of quantum physics.
Quantum cryptography offers the potential for unbreakable encryption. The key idea is that any attempt to eavesdrop on the communication will alter the quantum states of the transmitted data, thereby alerting the parties involved that the communication has been compromised.
Basic Concepts of Quantum Mechanics Relevant to Cryptography
Superposition
- Superposition is the ability of quantum particles (like photons) to exist in multiple states at once. For example, a photon can be in a state where it is simultaneously “0” and “1” in quantum cryptography. When measured, it collapses to one of the states, but until then, it remains in a superposition.
Entanglement
- Entanglement is a quantum phenomenon where two or more particles become linked, such that the state of one particle is directly related to the state of another, regardless of the distance between them. This property allows secure transmission of data because any change in one particle will instantly affect the other, providing a way to detect eavesdropping.
No-Cloning Theorem
- The no-cloning theorem states that it is impossible to create an identical copy of an unknown quantum state. This property is crucial for quantum cryptography because it prevents an eavesdropper from making an exact copy of the quantum data being transmitted, thus ensuring security.
How Quantum Cryptography Works
The core idea behind quantum cryptography is the exchange of quantum keys that can be used for encryption and decryption. These quantum keys are based on quantum states of particles, which are difficult to replicate or measure without disturbing them. If an eavesdropper attempts to intercept the key, they will cause disturbances that can be detected by the communicating parties.
The most common method for quantum cryptography is Quantum Key Distribution (QKD), which is based on the transmission of quantum bits (qubits) between two parties. These qubits are transmitted in quantum states that are either altered or destroyed when measured, making eavesdropping detectable.
Quantum Key Distribution (QKD)
Quantum Key Distribution (QKD) is the process that allows two parties to securely share a secret key, using the principles of quantum mechanics.
BB84 Protocol
- The BB84 protocol, developed by Charles Bennett and Gilles Brassard in 1984, is one of the first and most well-known quantum key distribution protocols. It relies on the transmission of polarized photons in two different bases (rectilinear and diagonal). After the photons are received, the parties compare their bases and keep the bits that match. Any eavesdropping would disturb the quantum states, thus revealing the presence of an intruder.
E91 Protocol
- The E91 protocol, introduced by Artur Ekert in 1991, uses quantum entanglement to generate a secure key. It requires two parties to share entangled particles and measure their states. If the measurements are correlated, the key is secure. This protocol also ensures that any eavesdropping will alter the state of the entangled particles, alerting the participants.
B92 Protocol
- The B92 protocol, introduced by Bennett in 1992, is simpler than BB84. It uses only two non-orthogonal states for encoding the key, making it less resource-intensive. The security of B92 is based on the no-cloning theorem and the fact that any attempt to measure the quantum state will introduce errors.
Applications of Quantum Cryptography
Quantum cryptography is primarily used for secure communication. Some key applications include:
- Government and Military Communications: Ensuring the secrecy of sensitive information.
- Banking and Financial Transactions: Protecting financial data from unauthorized access.
- Secure Voting Systems: Ensuring that voting information cannot be tampered with.
- Cloud Computing Security: Safeguarding data in cloud storage and services.
Advantages of Quantum Cryptography
- Unbreakable Encryption: Due to the principles of quantum mechanics, any eavesdropping attempt is immediately detectable.
- Resistance to Quantum Computers: Unlike traditional cryptographic methods, quantum cryptography is immune to the future capabilities of quantum computers.
- Provable Security: Security can be mathematically proven based on quantum mechanical laws.
Challenges and Limitations
- Infrastructure Requirements: Quantum cryptography requires specialized equipment such as photon detectors and quantum channels, which can be expensive and difficult to deploy on a large scale.
- Distance Limitations: Quantum signals degrade over long distances, making communication over vast areas difficult without the use of repeaters.
- Technology Readiness: While quantum cryptography is advancing, large-scale deployment is still a long way off due to the complexity of maintaining quantum states in practical environments.
Future of Quantum Cryptography
As quantum computing develops, quantum cryptography will play a critical role in securing data against quantum-based attacks. The integration of quantum cryptography into existing communication systems and infrastructure will require overcoming challenges in terms of hardware, network scalability, and standardization. However, as technology progresses, it holds the promise of creating an unprecedented level of security for digital communications.
Frequently Asked Questions
1. Is quantum cryptography completely secure?
Quantum cryptography is theoretically secure, as any attempt to eavesdrop on the transmission alters the quantum states and can be detected. However, practical implementations might still face challenges, particularly with noise and signal degradation over long distances.
2. What is the difference between quantum cryptography and classical cryptography?
Classical cryptography relies on mathematical problems that are difficult to solve (like factoring large numbers), while quantum cryptography leverages the principles of quantum mechanics, such as superposition and entanglement, to ensure security.
3. What is Quantum Key Distribution (QKD)?
Quantum Key Distribution is a technique that allows two parties to securely share a cryptographic key by transmitting quantum bits (qubits) through a quantum channel, ensuring that any eavesdropping attempt will be detected.
4. Can quantum cryptography be hacked?
While quantum cryptography offers theoretically unbreakable encryption, real-world implementations can be vulnerable to practical issues like hardware flaws, human error, or environmental interference. However, these risks are less severe than those in classical systems.
5. How does quantum cryptography benefit cybersecurity?
Quantum cryptography enhances cybersecurity by providing unbreakable encryption methods that cannot be cracked by even the most advanced computational techniques, including those that might be developed with quantum computers.
Latest Posts
- All Posts
- Software Testing
- Uncategorized




Categories
- Artificial Intelligence (5)
- Best IT Training Institute Pune (9)
- Cloud (2)
- Data Analyst (55)
- Data Analyst Pro (15)
- data engineer (18)
- Data Science (104)
- Data Science Pro (20)
- Data Science Questions (6)
- Digital Marketing (4)
- Full Stack Development (7)
- Hiring News (41)
- HR (3)
- Jobs (3)
- News (1)
- Placements (2)
- SAM (4)
- Software Testing (70)
- Software Testing Pro (8)
- Uncategorized (33)
- Update (33)
Tags
- Artificial Intelligence (5)
- Best IT Training Institute Pune (9)
- Cloud (2)
- Data Analyst (55)
- Data Analyst Pro (15)
- data engineer (18)
- Data Science (104)
- Data Science Pro (20)
- Data Science Questions (6)
- Digital Marketing (4)
- Full Stack Development (7)
- Hiring News (41)
- HR (3)
- Jobs (3)
- News (1)
- Placements (2)
- SAM (4)
- Software Testing (70)
- Software Testing Pro (8)
- Uncategorized (33)
- Update (33)