What is Gray Box Testing ?

What is Gray Box Testing ?
Gray box testing is a software testing approach that lies between black box testing and white box testing. It allows the tester to have partial knowledge of the internal workings of the system while still testing it from an external perspective.
1. White Box Testing vs. Black Box Testing vs. Gray Box Testing:
White Box Testing: Involves testing the internal structures, logic, and workings of an application. Testers have complete knowledge of the code, architecture, and system design. The focus is on checking the internal flow of data, algorithms, and code paths.
- Example: Unit testing, code coverage analysis, security testing.
Black Box Testing: Involves testing the application without any knowledge of the internal code. The tester only knows the inputs and expected outputs, but the internal workings of the system are hidden. The focus is purely on the user experience and functional behavior.
- Example: Functional testing, acceptance testing, usability testing.
Gray Box Testing: A mix of both approaches, where testers have partial knowledge of the internal workings (such as system design, architecture, or data flow) but they do not have access to the full code. This knowledge helps testers design more efficient and targeted test cases, but they still test the system from an external perspective, as an end-user would.
- Example: Integration testing, security testing, and some types of performance testing.
2. How Gray Box Testing Works:
In gray box testing, testers have some insights into the system architecture, design documents, or may be given access to certain parts of the code (like APIs or database schema). This knowledge can help them test the application more effectively.
For example, imagine testing an online banking application. As a gray box tester, you may have knowledge of the database schema (such as the names of tables or fields), so you can better understand how data is stored. You can use this information to test if the system is securely processing financial transactions, even though you don’t have full access to the source code.
3. Gray Box Testing Methods:
Access to Application Architecture or Design: Testers may be given access to design specifications, system diagrams, API documentation, or database schemas. This partial knowledge helps testers focus on areas of the application that are more prone to issues or vulnerabilities.
Test Case Design: Based on the knowledge gained from architecture documents, testers can design specific test cases. For example, understanding the data flow can help you test if sensitive data is handled properly (e.g., encryption during transmission or storage).
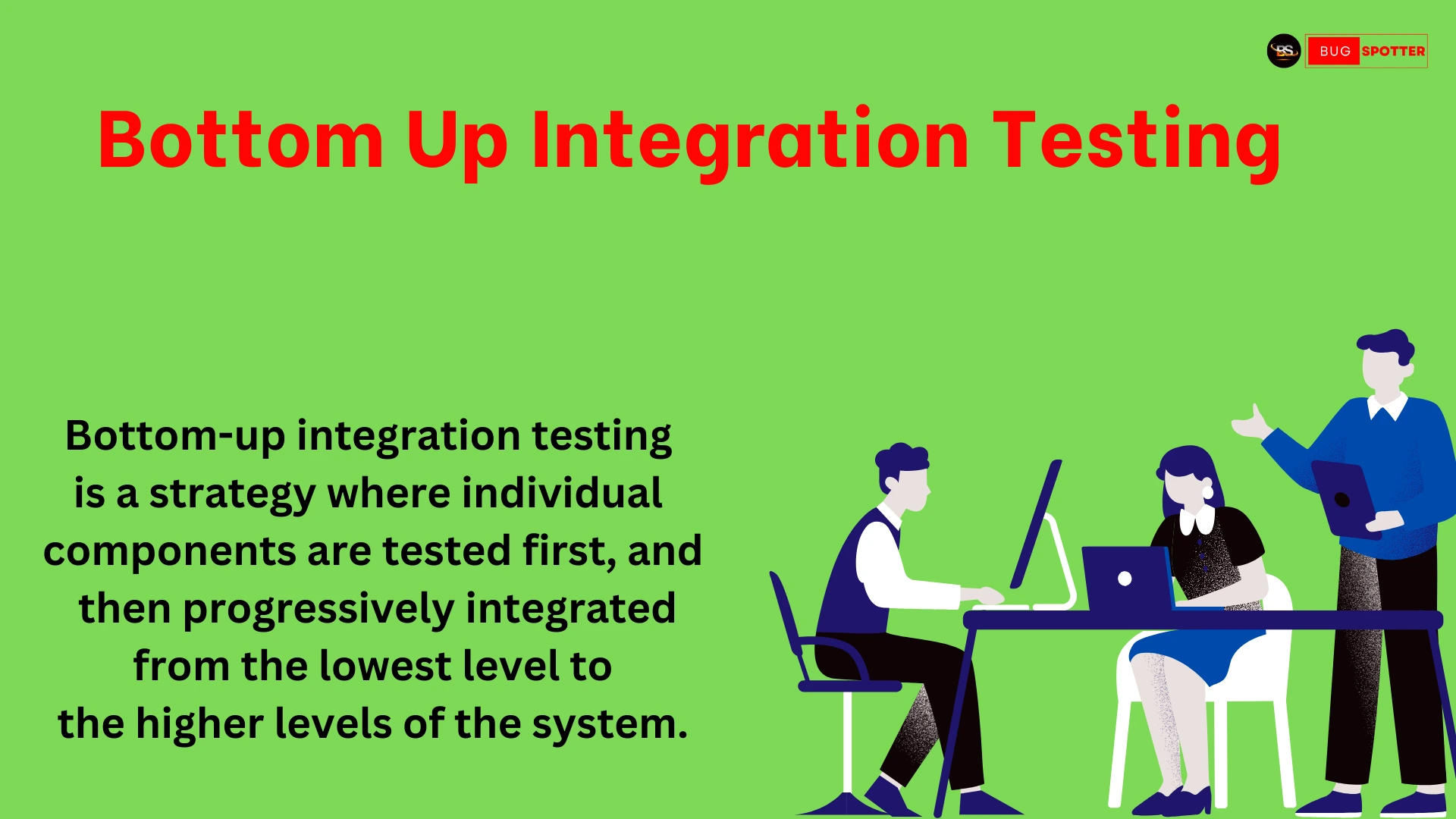
Integration Testing: Gray box testers often focus on testing how different modules or components of the system interact, especially when these interactions are not fully visible to the end user but are important for performance, security, or correctness.
Security Testing: A gray box tester can look at possible security vulnerabilities like injection flaws, insufficient authentication mechanisms, or access control vulnerabilities by using their knowledge of the architecture or underlying systems.
4. Common Gray Box Testing Techniques:
- Regression Testing: Gray box testers can execute a series of test cases to ensure that changes in one part of the system do not affect other parts.
- API Testing: If testers have knowledge of how the system’s APIs function, they can design tests that check for improper responses or failures when handling different types of requests.
- Security Vulnerability Testing: Gray box testers can identify security weaknesses by exploring potential vulnerabilities in areas such as input validation, authentication mechanisms, and data storage.
- Performance Testing: Understanding how the system processes data (e.g., database queries or transactions) allows testers to design tests that monitor load times, memory usage, and other performance metrics.
5. Advantages of Gray Box Testing:
- Efficiency: Since testers have some level of internal knowledge, they can design more efficient test cases that cover critical areas of the application, reducing testing time.
- Improved Test Coverage: Gray box testing can help find issues that might be overlooked in black box testing because it provides insight into the internal flow, while still ensuring the system behaves correctly from the user’s perspective.
- Better Security Testing: Gray box testers can more easily identify vulnerabilities in security (e.g., flaws in the authentication process, session management) by leveraging their understanding of the system’s architecture.
- Cost-Effective: It can be more cost-effective than white box testing, especially when full code access is not available. By focusing on specific areas based on system knowledge, testers can be more targeted and precise.
6. Disadvantages of Gray Box Testing:
- Limited Coverage: Since testers don’t have full access to the source code, they might miss certain logic flaws that could be detected with full code visibility (as in white box testing).
- Dependence on Documentation: If the system’s documentation or architecture information is incomplete or inaccurate, gray box testing could lead to false assumptions, which may lead to undetected defects.
- Complexity: Gray box testing can require testers to have knowledge of multiple disciplines (e.g., coding, system design, security) to perform effectively, which might be a challenge for some testing teams.
7. Example Scenarios of Gray Box Testing:
- E-commerce Website: The tester knows the database schema, such as the structure of product records, user data, and transaction history. They can create test cases to verify if sensitive information (like passwords or payment details) is stored or transmitted securely.
- Mobile App: The tester might have access to the app’s API documentation, allowing them to design tests that validate how the mobile app communicates with the backend server (e.g., checking for proper API response codes and error handling).
- Cloud Service: A gray box tester might know the cloud infrastructure setup (e.g., database, storage, and services), so they can test for performance bottlenecks, security vulnerabilities, and system interactions, even though they can’t access the internal code of the cloud-based service.
8.Tools Used in Gray Box Testing:
Gray box testers often leverage tools from both black box and white box testing. Some common tools include:
Fuzz Testing Tools: These tools are used to test the system with a wide range of random or invalid inputs to identify issues such as crashes, unexpected behavior, or security vulnerabilities.
Postman/Swagger: Used for API testing, these tools help in testing various API endpoints and checking if the API responds correctly with expected inputs or invalid data.
Burp Suite: This security testing tool is used for finding vulnerabilities such as XSS (Cross-Site Scripting), SQL Injection, and other web security issues, especially when testers have partial knowledge of the system.
OWASP ZAP: This open-source security testing tool helps detect vulnerabilities in web applications, such as those related to data flow and security misconfigurations, which can be tested using a gray-box approach.
Wireshark: Used for network analysis, this tool helps testers examine data flows between the client and server to ensure that sensitive information (e.g., passwords, personal data) is encrypted and transmitted securely.
9.Real-World Scenarios for Gray Box Testing:
Web Application Security: Consider a situation where you are testing an online banking system. The tester might know that the system uses a third-party payment processor. Even without knowing the code behind payment processing, the tester can simulate malicious inputs (e.g., sending corrupted payment data) to check for vulnerabilities like SQL injection or session hijacking.
API Testing: If the system uses external APIs (for example, for weather data in a travel app), the tester might have access to API documentation that describes endpoints and expected responses. With this knowledge, they can design tests to verify if the API works as expected under various conditions (e.g., handling invalid or unexpected data gracefully).
Database Integration Testing: Gray box testers can have partial access to database schemas (e.g., knowing which tables store user information or transaction data). By focusing on these areas, they can test if data is inserted, retrieved, and processed correctly, even if they don’t know the complete database logic or the business rules applied on the backend.
Testing Cloud Services: In cloud-based applications, gray box testing can be used to examine the interactions between cloud services (e.g., AWS or Azure services) and the application. While testers might not have full access to the underlying cloud infrastructure, they can still test for issues like data leaks, unauthorized access, or performance issues during high traffic.
Latest Posts
- All Posts
- Software Testing
- Uncategorized




Categories
- Artificial Intelligence (5)
- Best IT Training Institute Pune (9)
- Cloud (2)
- Data Analyst (55)
- Data Analyst Pro (15)
- data engineer (18)
- Data Science (104)
- Data Science Pro (20)
- Data Science Questions (6)
- Digital Marketing (4)
- Full Stack Development (7)
- Hiring News (41)
- HR (3)
- Jobs (3)
- News (1)
- Placements (2)
- SAM (4)
- Software Testing (70)
- Software Testing Pro (8)
- Uncategorized (33)
- Update (33)
Tags
- Artificial Intelligence (5)
- Best IT Training Institute Pune (9)
- Cloud (2)
- Data Analyst (55)
- Data Analyst Pro (15)
- data engineer (18)
- Data Science (104)
- Data Science Pro (20)
- Data Science Questions (6)
- Digital Marketing (4)
- Full Stack Development (7)
- Hiring News (41)
- HR (3)
- Jobs (3)
- News (1)
- Placements (2)
- SAM (4)
- Software Testing (70)
- Software Testing Pro (8)
- Uncategorized (33)
- Update (33)